Comodo Kill Switch
Hi all I have recently followed the guides on this forum as to how to setup a kill switch with Comodo, I want to tunnel all traffic through AirVPN. Build your own VPN kill switch in Windows using Comodo - Duration: 6:23. Sam R 5,306 views.
January 3, 2019By ComodoMalware or malicious software is an infectious code created by malware authors to attack devices, as well as damage, distort and steal important data. The impact of a malware attack might could be simple to or complex. Types of malware includes: computer virus, trojans, rootkits, keyloggers, adware, ransomware, worms, etc.
Security experts have built efficient malware removal tools to aid users in protecting devices. In this article we will share about the best free malware removal tools of 2020 with the ability to isolate and terminate malware attacks.
Conventional antivirus alone cannot protect devices and data. A complete malware removal suite is essential to stay protected from malware attacks. Some malware are capable of escaping detection, however, security experts have developed sophisticated malware removal tools.
Following are the top five malware removal tools:
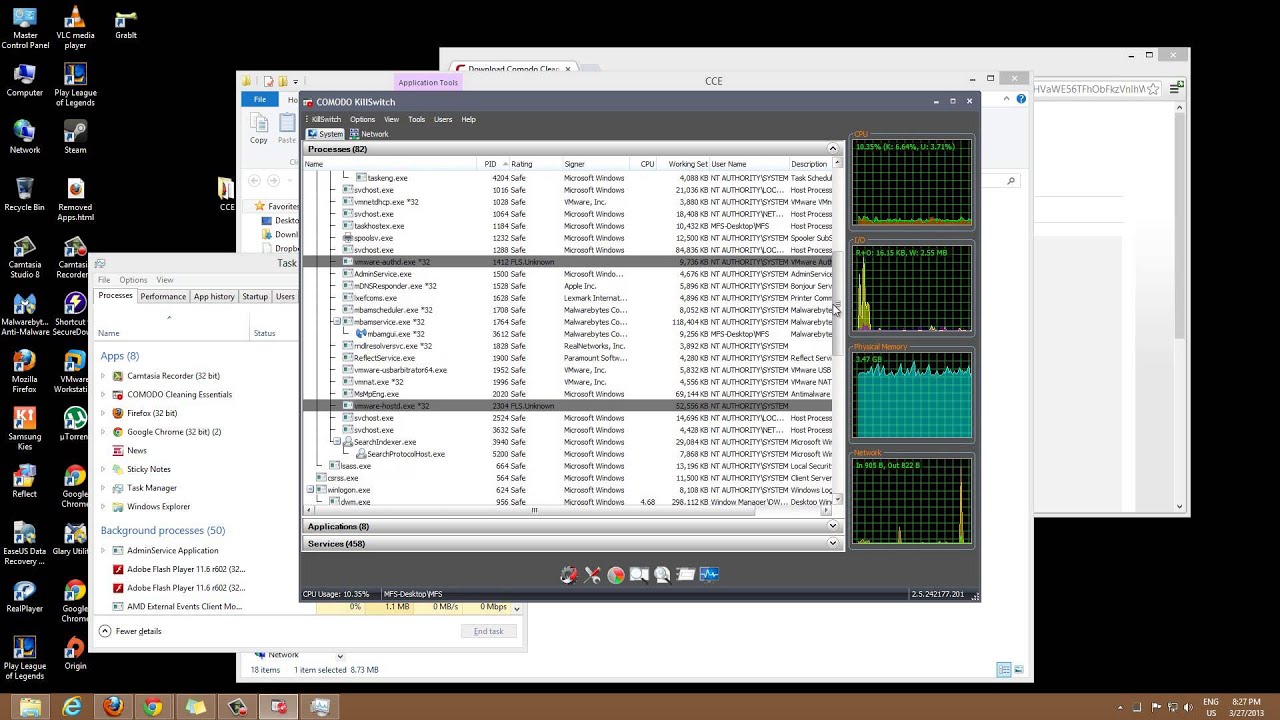
Comodo Forensic Analysis:Comodo Cleaning essentials is a computer security suite developed to detect and terminate malware and suspicious processes from computers that are infected. It is a portable software which can be run instantly by using a USB key. The kill switch feature is an advanced system monitoring tool that uses a whitelist database to isolate suspicious processes at an accurate level to enhance IT operational efficiency and therefore mitigating the time taken to troubleshoot an infected endpoint system. It also features a malware scanner that removes the viruses, hidden untrusted files, malware registry keys, rootkits and the like from the infected system. The scanner implements the most sophisticated future-proof heuristic methods to identify the hidden viruses. It is also capable of detecting hidden services, drivers loaded while starting up a system. It also provides forensic level graphs and stats to analyze the internal processes and resource usage at a granular level.
Malwarebytes Anti-Malware – Next Malwarebytes’ free Anti-malware. When you are installing Malwarebytes for the first time you will be entitled a 14- day trial of the premium version, which includes real-time scanning protection from ransomware threats., however the free version reverts back to basic after two weeks. The premium version can be updated manually by paying a subscription fee.
Bitdefender Antivirus Free Edition – Bitdefender Antivirus provides some of the most robust and efficient features to scan suspicious files. If any displays abnormal functions, it is identified by malware removal engine and immediately isolated and terminated.
Adaware Antivirus Free – This features an isolated virtual environment where files and programs that are found suspicious are analyzed to check for any malicious behavior through a process called heuristic analysis. This helps the user to ensure the malware is safely contained within the virtual environment without affecting the normal operations of the computer. Adaware Antivirus can also scan downloads even before the user installs it on the system.
Emsisoft Emergency Kit – It’s a portable security app that can be carried in a USB stick or over a cloud storage service. It archives a database of threats and while using the Emsisoft for cleaning the PC, there should be internet connection to enable the software to check for updates. Once it has been updated, it scans the PC for threats and isolates anything that is found suspicious. A reboot is done immediately, and the files will be removed.
Conclusion:
Malware removal software is critical to protect devices from malicious threats and stay ahead of dangerous malware attacks. However, choosing the right one is key. We have done extensive research and listed the top 5 free malware removal tools, that are efficient to protect your PC from all kinds of threats.
Latest Version:
Comodo Cleaning Essentials 10.0.0.6111 (64-bit) LATEST
Requirements: Berpikir dan menjadi kaya pdf merge.
Windows XP 64 / Vista 64 / Windows 7 64 / Windows 8 64 / Windows 10 64
Author / Product:
Comodo Group, Inc / Comodo Cleaning Essentials (64-bit)
Old Versions:
Filename:
cce_x64.zip
Details:
Comodo Cleaning Essentials (64-bit) 2020 full offline installer setup for PC
KillSwitch
An advanced system monitoring tool that allows users to identify, monitor and stop potentially unsafe processes that are running on endpoint systems. Uniquely for a product of its type, KillSwitch leverages Comodo's huge whitelist database to isolate untrusted processes with an extremely high degree of accuracy – improving IT operational efficiency by reducing false positives and cutting the amount of time spent troubleshooting an endpoint machine.
Malware scanner
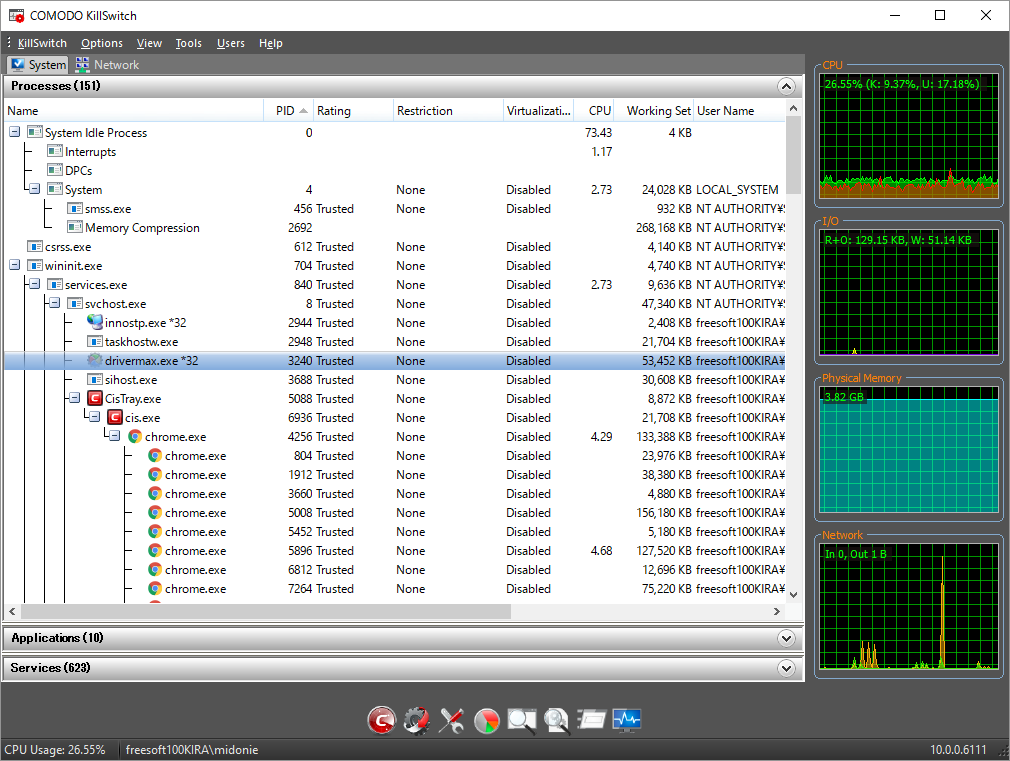
Fully featured malware scanner capable of unearthing and removing viruses, rootkits, hidden files and malicious registry keys hidden deep within a system. The scanner is highly configurable, uses the latest heuristic techniques to detect previously unknown viruses, features first-class malware removal capabilities and is capable of detecting hidden drivers and services loaded during system start-up.
Features and Highlights
- Instantly identify and stop every untrusted process
- Running on an endpoint with a single click
- Powerful antivirus scanner capable of removing malware, rootkits, hidden files and malicious registry keys hidden deep within a system
- Forensic level stats and graphs allow internal processes and resource usage to be analyzed with unrivaled granularity
- Integration with Comodo cloud scanners provides real-time safety verdicts for unknown processes
- Perfect for ensuring network endpoints are totally clean of threats
- No installation required – can run direct from USB or user desktop via RDP